Virtual World?
According to Wikipedia.com: “A virtual world (also called a virtual space) is a computer-simulated environment[1] which may be populated by many users who can create a personal avatar,[2] and simultaneously and independently explore the virtual world, participate in its activities and communicate with others.[3][4] These avatars can be textual,[5] graphical representations, or live video avatars with auditory and touch sensations.[6][7] Virtual worlds are closely related to mirror worlds.”
At this point, there are a number of issues still to be worked out. Privacy and security are one of the main issues. Which is where session keys come into play.
Session Keys
TechTarget.com explains:
The session key is used for only one session. It is then discarded, and a new key is randomly generated for the next session. Public keys or asymmetric encryption, by contrast, use two keys — a public key and a private key — instead of a single key to secure data communication between two parties over an open network.
What is a session?
A session is an interaction between a user and a web server characterized by an exchange of information. This exchange may be in the form of a request-response between a browser and web server.
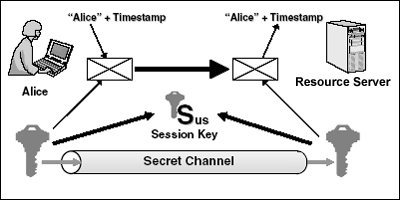 In this example, Alice encrypts a message she is sending with its current
In this example, Alice encrypts a message she is sending with its currenttimestamp using a randomly generated session key. When the server receives
the message, it decrypts it using that same symmetric key to check her name
and timestamp. If those are OK, the server authenticates the message.
Alternatively, the interaction may not involve a request or response between the two parties. For instance, when a user signs in to a web service, the session is essentially an exchange of information that results in the user signing in and the server storing this information for later use.
Another kind of session is a browser session, which is when someone makes a request to a web server. Here, a session begins when a user first requests a page from a web server and is completed when that browser has sent over all the packets of information the server requested, such as when a user logs in to a website. This is considered a session because it is a series of interactions with the website requiring a data connection.
Other kinds of sessions include the following:
- Hypertext Transfer Protocol (HTTP) sessions. An HTTP session is a series of interactions between a user’s browser and a web server that persists beyond a single page view and enables the server to track a user’s activity.
- Transmission Control Protocol (TCP) session. A TCP session is a logical connection between two network hosts established by the exchange of transport layer segments.
- Telnet remote login session. A Telnet remote login session is a method used to connect to and interact with a remote server.
Cryptography key terms to know
The most important terms to know when discussing cryptography, including session keys, are the following:
- Encryption. The process of converting data into a format that is unreadable without special knowledge.
- Decryption. The process of converting encrypted data back to its original, readable format.
- Symmetric key. A single, shared key used by two parties to encrypt and decrypt data.
- Asymmetric key. Two separate keys used to encrypt and decrypt data.
Advantages of cryptographic session keys
cryptography is an essential tool in the fight against identity theft that is used to protect information in a wide range of applications, such as electronic commerce, information security and data storage. Cryptography uses keys to encrypt and decrypt data. The most common type of cryptography key is a symmetric key, which uses the same key to encrypt and decrypt data — as opposed to asymmetric keys, which use a separate key for encryption and decryption.
Generated using a symmetric algorithm, sessions keys have number of advantages:
- The major advantage of session keys is they are convenient to use. Session keys can be a single fixed key, or they can be generated dynamically from a set of existing keys.
- Session keys offer added protection because the key is discarded after it has been used to establish a secure communication channel, such as during a Transport Layer Security (TLS) connection.
- Asymmetric algorithms usually take longer to compute than symmetric algorithms. Since session keys are single-use symmetric keys, they are much faster to use for particular applications, including for storing caches of temporary data.

Disadvantages of session keys
Sessions keys are not without their disadvantages, including the following:
- The biggest disadvantage of using session keys is they are not as secure as public keys due to their simplicity. Using a session key for more than one session may compromise it.
- Another disadvantage of using a session key to encrypt data is that it is vulnerable to eavesdropping and compromise. As a symmetric key, a session key is used to both encrypt and decrypt data. This makes information vulnerable should bad actors intercept the key in transit through the network or steal it when stored in the memory of a server.
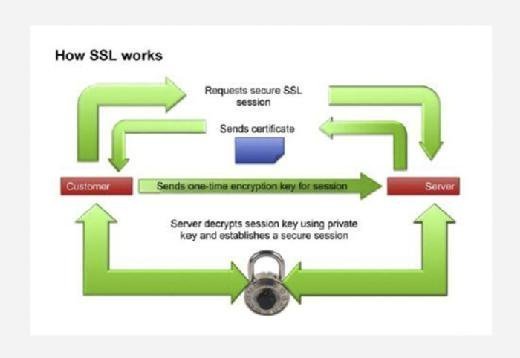
HTTPS encryption and session keys
HTTP over Secure Sockets Layer, or SSL, also known as HTTP Secure (HTTPS), is a web protocol that encrypts data sent between a browser and website. The encryption gets the data to its destination securely so it can’t be intercepted and read in transit.
By adding an encryption layer to the connection, HTTPS ensures a connection is private. With HTTPS, when a browser sends a request to access a website, it generates a session key. The session key encrypts sent data and decrypts that data when it is received.
For instance, if users enter their checking account information to buy items online, their browser will encrypt that information using a session key. The website’s server will then decrypt it using the session key it received from the browser.
How does a TLS handshake work?
In order to create a secure connection between two computers, a series of steps must be taken. Called the TLS handshake, these steps are the first thing that occurs when connecting to a website with HTTPS.
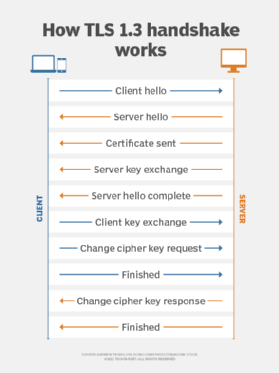
Thinks of a TLS handshake as a protocol that enables two computers to agree on how they will communicate. If the handshake fails, then the connection is not secure. While a TLS handshake can fail in many different ways, the most common reason is due to misinformation passed back and forth between two communicating computers.
A TLS handshake involves the following three steps:
- The server sends its SSL certificate to the client.
- The client checks the certificate.
- The client encrypts a random number with a public key.
The session key encrypts the bulk of the data transmitted in the TLS handshake and is generated and negotiated independently of the protocol version and cipher suite selected by the clients and servers. As a result, the session key is the same for all connections established between two peers that support the same protocol version.
Closely related concepts
Master encryption key (MEK). A MEK is an encryption key that protects other encryption keys. A cryptographic key used to generate a large number of other keys, a master key is usually not directly used for encryption or decryption. Rather, it is used to generate session keys that are then used for communications. Since session keys are only needed for a short period of time, a master key is more practical than a per-use key.
Key encryption key (KEK). A KEK is used to encrypt other keys, such as the data encryption key or the traffic encryption key, that are used to encrypt sensitive data.
Content encryption key (CEK). A CEK is a key that may be further encrypted using a KEK. The CEK is used to encrypt content for storage or transmission, including content in the form of messages, images, audio, etc.
Randomness Generators are the next step in generating those session keys and bringing Zuckerberg’s digital experience closer to fulfillment.
Zuckerberg’s Concept
In October of 2021, Mark Zuckerberg laid out his plans for the next phase of the digitized human experience. It would be immersive in a true sense virtual world accepted to have realness in its own right, where people live rather than simply plugging in.
In his 2021 Founder’s Letter to stakeholders, Zuckerberg wrote,
“The defining quality of the metaverse will be a feeling of presence ke you are right there with another person or in another place.”
But what does this mean from a practical perspective, exactly? The metaverse will blur the lines between mundane and virtual realities by leveraging VR and AR technologies.
Once the architects of the future build the metaverse, residents will be able to move through, engage with and socialize within digital spaces just as they would in real life.
Needless to say, people have opinions about it, and much of their conversation stops at the theoretical. The metaverse is for now a far-off idea. However, there’s little doubt that Pandora’s Box will eventually open.
As we’ve seen time and time again, humans are too curious to leave the potential for innovation unexplored. The building blocks for this new world are barely defined let alone ready to stack. The architects of the future are missing one of the core tools they’ll need to assemble the metaverse accessible randomness.
Understanding randomness’s role in metaverse construction
As Rabindra Ratan and Dar Meshi neatly summed up in an article for Bright Think,
“Web 3.0 will be the foundation for the metaverse. It will consist of blockchain-enabled decentralized applications that support an economy of user-owned crypto assets and data.”
Randomness is a core aspect of cryptography, which in turn underlies many technologies that will be foundational to metaverse construction ost notably, blockchain.
Blockchain’s functionality hinges upon cryptographic features such as randomly generated public-private key pairs and the application of nonce (number used once) in proof-of-work validation.
For a simple example, we can turn to crypto wallet keys. These public-private key pairs are randomly generated to prevent a malicious actor from guessing them and gaining access to users’ hard-earned crypto.
Without randomness to provide security, a single lucky guess from the hacker could lead to crippling financial losses for the user.
As Henrique Centiero noted for Level Up in mid-2021, random numbers,
“remove the reasoning and predictability of generating numbers, making it hard for an attacker to access the information. The attacker will have no way or mechanism to reason how those numbers were generated, making it harder to hack and discover how the cryptographic keys were created.”
Keys require randomness to be secure and since they already have it, welcoming users to the metaverse should be a simple matter, right?
Wrong. While blockchain currently offers key security, it falls short on privacy. When users leverage blockchain technologies, they can rest assured that every transaction will be secure, auditable and transparent.
However, transparency cuts both ways without further privacy measures, a user who makes a purchase using blockchain leaves themselves open to uncomfortable scrutiny.
Think of it this way. If you stopped at a local coffee shop before work, would you want the barista to see your personal banking history as he makes your cappuccino?
If the metaverse is to be a world people can live in, it needs to offer the comfort of privacy. Every feature within every attraction of every digital hub needs to leverage randomness to provide a truly secure and private experience. Otherwise, people may not even visit, let alone choose to take up residence in the metaverse.
If some DApps decide not to prioritize privacy ahead of the metaverse launch, users might become wary as they traverse digital worlds, worrying every time they enter a new hub that their privacy may be compromised.
Thus, we can understand that randomness is fundamental to constructing a universally secure, trustworthy and private metaverse. Just as real-world contractors require bricks and mortar to build stunning skyscrapers, so too do metaverse architects need randomness generators to make their visions a (virtual) reality.
The problem is that randomness isn’t exactly easy to achieve and some architects are more fortunate in their access than others.
In the metaverse’s earliest days, accessible randomness is an equality imperative
Achieving randomness at scale is a challenging task. According to DappRadar’s 2021 report, the number of unique active wallets connected to DApps topped 2.7 million by the end of the year, and blockchain virtual worlds achieved a record market cap of $3.6 billion.
The sheer demand associated with privacy-preserving randomness generation is high now and will only grow as the need for more DApps, virtual spaces and metaverse experiences increases.
So, what are the architects of the future to do? Theoretically, each DApp development team could create its own randomness generator. However, doing so would take up a great deal of time, effort and resources.
For some players, the investment will be feasible. Wealthy corporate players like Meta, Microsoft and Google have deep pockets and considerable motivation to stake their claim on the metaverse. They can sink resources into randomness acquisition and not think twice of the expense.
But for independent developers who don’t have the advantage of corporate wealth, obtaining the tools necessary for metaverse construction simply isn’t that easy.
At best, such architects might be slow to start construction. At worst, they’ll be reduced to wandering worlds derived from corporate imagination, always knowing that they could have built something special if they only had the chance.
This cannot come to pass. The metaverse is meant to be a place of infinite potential. From a philosophical standpoint, the only limits placed on metaverse architects should be those of imagination.
If a person can dream it, they should be capable of building it. However, when randomness a core ‘building block’ for the metaverse isn’t universally accessible, only those with deep pockets will have the chance to build.
Corporate dominance would set the groundwork for a modern fiefdom. Industry giants might see the metaverse as an opportunity to expand their symbolic domination and increase their profits.
These players could attempt to monopolize the digital landscape, expand their brand’s identity into the virtual world, and claim the metaverse as corporate property.
But to reduce the metaverse to a playground for commercial giants would be to utterly degrade its founding spirit. People should have the right to be free from centralized control and build their worlds in the metaverse, limited only by the constraints of imagination.
Thus, we come to the only conclusion that to live up to the metaverse’s promise, we need to make randomness universally accessible.
A universally-accessible and decentralized randomness generator could empower metaverse visionaries to ensure honesty, fairness, transparency and privacy as they construct their own virtual worlds.
Opportunities will no longer be restricted to wealthy corporate players. Individual builders can work unhindered, build a community and develop a metaverse playground that welcomes and supports everyone not just tech behemoths.
The metaverse isn’t much more than a dream at the moment. However, accessible randomness will empower digital architects to start building the first structures of the metaverse and deliver the digital worlds we imagine into (artificial) reality.
Featured Image: Shutterstock/studiostoks
Via this site.
Disclaimer:
Although the material contained in this website was prepared based on information from public and private sources that EcomiCrush.com believes to be reliable, no representation, warranty or undertaking, stated or implied, is given as to the accuracy of the information contained herein, and EcomiCrush.com expressly disclaims any liability for the accuracy and completeness of the information contained in this website.

