New Lace Wallet Security Feature
Cardano co-founder willing to put his money where his mouth is. Charles Hoskins says he’ll bet $1million to prove the efficiency of the new security feature being proposed by Lace wallet.
Lace, built by Cardano developer Input Output Hong Kong (IOHK), is a lightweight multi-chain crypto wallet that aims to seamlessly connect everything in Web2 and Web3 to a single interface.
Hoskinson says in a new YouTube update that it’s “extraordinary” to him what happened with the recent hack on the password management firm LastPass.
LastPass noted in an update last week that an unauthorized entity gained access to a third-party cloud-based storage service that the company uses to store archived backups of its production data.
The hacker obtained “basic customer account information and related metadata including company names, end-user names, billing addresses, email addresses, telephone numbers, and the IP addresses from which customers were accessing the LastPass service,” according to LastPass CEO Karim Toubba.
Hoskinson calls it a “screw up” on LastPass’s part and says it’s “pretty dirty what happened.”
The Cardano co-creator says “it’s a shame” that Pretty Good Privacy (PGP), an encryption program, isn’t a standard.
Says Hoskinson,
“When… Lace wallet starts supporting PGP encryption of paper wallets, I’m going to take some ADA – probably a million dollars worth of it – put it into a paper wallet encrypted with PGP and publicly post it on my Twitter so you guys can try to break it. I’m very confident in those standards. Master passwords, even if they’re quite long, it’s just a dead standard, and it shouldn’t be done anymore.”
What Is PGP Encryption and How Does It Work?
Pretty Good Privacy (PGP) is an encryption system used for both sending encrypted emails and encrypting sensitive files. Since its invention back in 1991, PGP has become the de facto standard for email security.
The popularity of PGP is based on two factors. The first is that the system was originally available as freeware, and so spread rapidly among users who wanted an extra level of security for their email messages. The second is that since PGP uses both symmetric encryption and public-key encryption, it allows users who have never met to send encrypted messages to each other without exchanging private encryption keys.
If you want to improve the security of your email messages, PGP offers a relatively easy and cost-effective way to do this. In this guide, we’ll show you how.
- PGP Encryption Uses
- Pros and Cons
- PGP Solutions
-
How Does PGP Encryption Work?
PGP shares some features with other encryption systems you may have heard of, like Kerberos encryption (which is used to authenticate network users) and SSL encryption (which is used to secure websites).
At a basic level, PGP encryption uses a combination of two forms of encryption: symmetric key encryption, and public-key encryption.
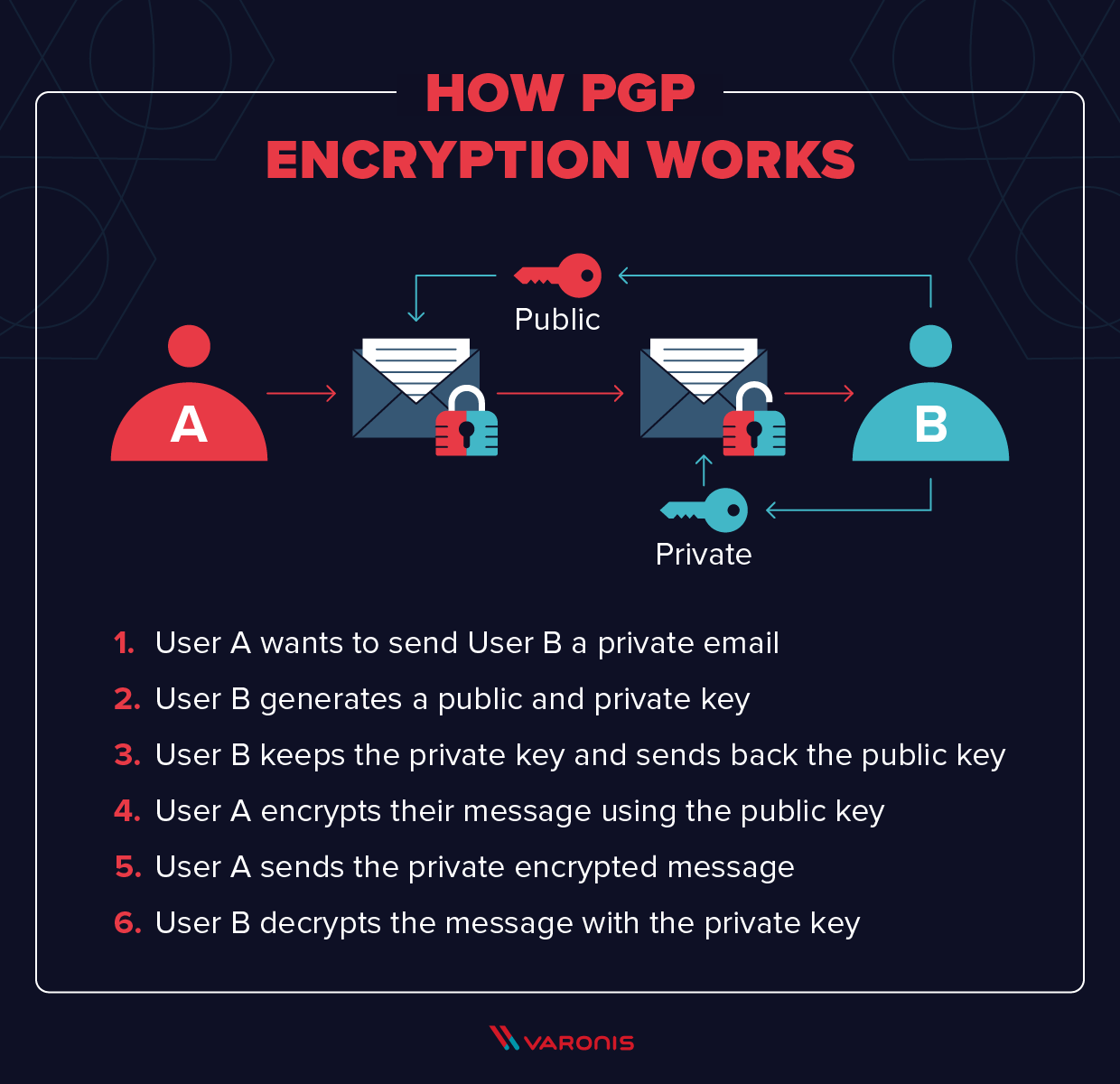
In order to understand how PGP works, it’s useful to look at a diagram:
The mathematics behind encryption can get pretty complex (though you can take a look at the math if you like), so here we’ll stick to the basic concepts. At the highest level, this is how PGP encryption works:
- First, PGP generates a random session key using one of two (main) algorithms. This key is a huge number that cannot be guessed, and is only used once.
- Next, this session key is encrypted. This is done using the public key of the intended recipient of the message. The public key is tied to a particular person’s identity, and anyone can use it to send them a message.
- The sender sends their encrypted PGP session key to the recipient, and they are able to decrypt it using their private key. Using this session key, the recipient is now able to decrypt the actual message.
This might seem like a strange way to do things. Why would we encrypt the encryption key itself?
Well, the answer is pretty simple. Public key cryptography is much, much slower than symmetric encryption (where both the sender and recipient have the same key). Using
symmetric encryption requires, though, that a sender share the encryption key with the recipient in plain text, and this would be insecure. So by encrypting the symmetric key using the (asymmetric) public-key system, PGP combines the efficiency of symmetric encryption with the security of public-key cryptography.
Example of PGP Encryption in Action
In practice, sending a message encrypted with PGP is simpler than the above explanation makes it sound. Let’s take a look at ProtonMail – as an example.
ProtonMail natively supports PGP, and all you have to do to encrypt your email is to select Sign Mail. You will see a padlock icon on the subject line of their emails. The email will look like this (the email addresses have been blurred for privacy reasons):
ProtonMail – like most email clients that offer PGP – hides all of the complexity of the encryption and decryption of the message. If you are communicating to users outside of ProtonMail, you need to send them your public key first.
And so, although the message was sent securely, the recipient does not have to worry about the complexities of how this was done.
PGP Encryption Uses
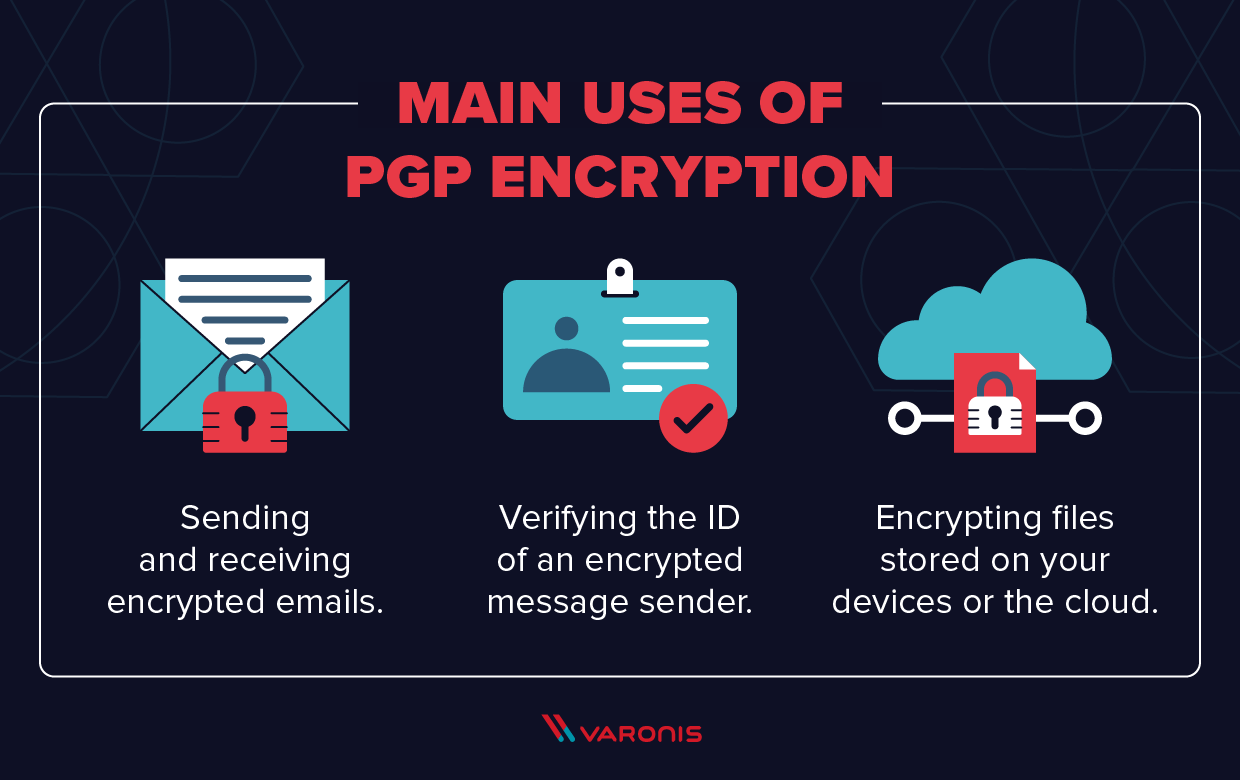
There are, essentially, three main uses of PGP:
- Sending and receiving encrypted emails.
- Verifying the identity of the person who has sent you this message.
- Encrypting files stored on your devices or in the cloud.
Of these three uses, the first – sending secure email – is by far the dominant application of PGP. But let’s take a brief look at all three
Encrypting Emails
As in the example above, most people use PGP to send encrypted emails. In the early years of PGP, it was mainly used by activists, journalists, and other people who deal with sensitive information. The PGP system was originally designed, in fact, by a peace and political activist named Phil Zimmermann, who recently joined Startpage, one of the most popular private search engines.
Today, the popularity of PGP has grown significantly. As more users have realized just how much information corporations and their governments are collecting on them, huge numbers of people now use the standard to keep their private information private.
Digital Signature Verification
A related use of PGP is that it can be used for email verification. If a journalist is unsure about the identity of a person sending them a message, for instance, they can use a Digital Signature alongside PGP to verify this.
Digital signatures work by using an algorithm to combine the sender’s key with the data they are sending. This generates a “hash function,” another algorithm that can convert a message to a block of data of fixed size. This is then encrypted using the sender’s private key.
The recipient of the message can then decrypt this data using the sender’s public key. If even one character of the message has been changed in transit, the recipient will know. This can indicate either the sender is not who they say they are, that they have tried to fake a Digital Signature, or that the message has been tampered with.
Featured Image: Shutterstock/ValDan22
Disclaimer: Although the material contained in this website was prepared based on information from public and private sources that EcomiCrush.com believes to be reliable, no representation, warranty or undertaking, stated or implied, is given as to the accuracy of the information contained herein, and EcomiCrush.com expressly disclaims any liability for the accuracy and completeness of the information contained in this website.